Howto Block Entire TLDs in Postfix
Reading time: 4 minutes
Blocking or blacklisting entire Top Level Domains (TLDs) in Postfix mail server may have a big impact to reduce spam, phishing, and other unwanted emails. Dependent on the use case of your systems it is a valid and effective solution. The only drawback is, to monitor your email traffic and check, whether valid emails from blocked TLDs are sent to your systems. Blocking a whole TLD is mostly a temporary thing, as the bad guys move on if the domains on a specific TLD are not usable for their cases.
This tutorial is focuses on senders (users/clients) using this TLDs. If you want to block mail servers using uncommon TLDs for their hostname in setup, this is not the right solution. Check this tutorial: Howto block mailservers using uncommon TLDs in hostname through Postfix
Setup using PCRE and Regexp Table Format
The setup on a single Postfix mail server is pretty straightforward and can be updated, extended, or removed at any time without big changes.
First of all, create a file called something like /etc/postfix/reject_domains
and add the relevant Top Level Domain (TLD) like .xyz, the
word REJECT, and the message like “We reject all mails from .xyz domains”.
Dependent on your preferences you can use Perl Compatible Regular Expressions
(PCRE) Format or built-in
Regexp. I’ll explain you both.
PCRE Table Format Setup
Dependent on your Linux distribution you may need to install an additional package called something like postfix-pcre as Perl Compatible Regular Expressions (PCRE) support is optional in Postfix. As the regexp format is pretty similar, you can skip this and use the second one.
You can use PCRE format to define regular expressions for TLDs.
Your /etc/postfix/reject_domains may look like this:
/\.date$/ REJECT We reject all mails from .date domains
/\.pro$/ REJECT We reject all mails from .pro domains
/\.top$/ REJECT We reject all mails from .top domains
/\.wtf$/ REJECT We reject all mails from .wtf domains
/\.xyz$/ REJECT We reject all mails from .xyz domains
Now edit your Postfix main configuration /etc/postfix/main.cf and add a rule
to your smtpd_sender_restrictions:
smtpd_sender_restrictions =
check_sender_access pcre:/etc/postfix/reject_domains
pcre: parameter tells Postfix, that the regular expression in the file is
in Perl PCRE
Table.
As the last step you have to reload/restart Postfix to enable this setup:
# using systemd
service postfix reload
# or just postfix
postfix reload
Regexp Table Format Setup
Compared to PCRE, Regexp Tables are built-in Postfix and enabled by default. That’s why I prefer using Regexp instead of PCRE and I’m used to programming languages using this format for regular expressions.
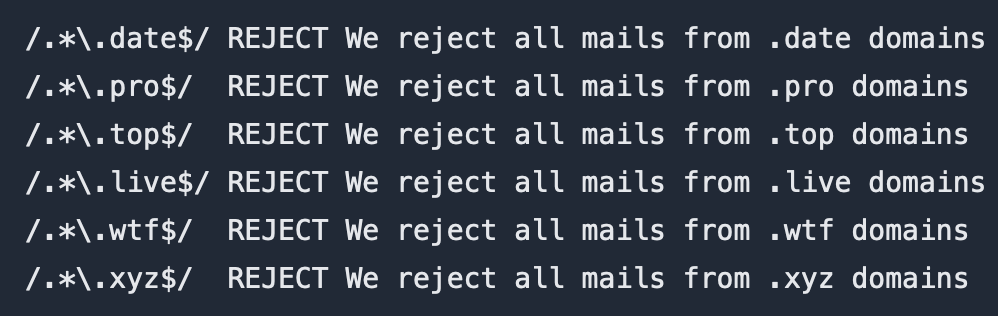
You define one regular expression for every TLD per line. Your
/etc/postfix/reject_domains may look like this:
/.*\.date$/ REJECT We reject all mails from .date domains
/.*\.pro$/ REJECT We reject all mails from .pro domains
/.*\.top$/ REJECT We reject all mails from .top domains
/.*\.live$/ REJECT We reject all mails from .live domains
/.*\.wtf$/ REJECT We reject all mails from .wtf domains
/.*\.xyz$/ REJECT We reject all mails from .xyz domains
Now edit your Postfix main configuration /etc/postfix/main.cf and add a rule
to your smtpd_sender_restrictions:
smtpd_sender_restrictions =
check_sender_access regexp:/etc/postfix/reject_domains
regexp: parameter tells Postfix, that the regular expression in the file is in
Regexp Table format.
As the last step you have to reload/restart Postfix to enable this setup:
# using systemd
service postfix reload
# or just postfix
postfix reload
To block or not to block a whole TLD
Dependent on the use case of your server, it may be appropriate to block TLDs for a short or even longer period. Take a look at your logs, maybe a monitoring system, which can analyze and display such information.
By using MailMum and this way analyzing email traffic to the systems I’m responsible for, I could get the same insights as Brian Krebs. Also, you can check Spamhaus World’s Most Abused TLDs to get a feeling, of what to look for.
Providing separated (virtual) servers for single customers which a specific user base, you can take advantage of this simple and pretty effective way to block senders using this technique.
Summary
Dependent on your mail systems setup, you can use TLD blocking by rejecting specific TLDs or Domains to reject the traffic. It may be a valid solution for one use case and a wrong one for big providers hosting thousands of different customers with their different use cases on a system or even a cluster.
Newsletter
See Also
- Sending Test Emails from Shell
- Monitoring your Local Postfix Blacklist with Munin
- Manage Postfix Mail Server Queues like a Pro
- Blacklisting Single Hosts, IP Addresses, and even Networks in Postfix
- Whitelisting single Hosts, IP Addresses, and even Networks in Postfix